How to connect wireless to eduroam manually: Difference between revisions
(Fixed Keychain link) |
mNo edit summary |
||
| Line 24: | Line 24: | ||
We've created step-by-step instructions for how to configure some of the most common clients. | We've created step-by-step instructions for how to configure some of the most common clients. | ||
NB! | NB! Mac users experiencing problems with eduroam may have expired certificates on their computer. To solve this, try to enter the keychain and select certificates at the bottom left. These certificates will have names like nps or radius.uib.no. [[Mac OS X: How to delete keys from the Keychain|Here's more information about how to delete keys from the Keychain on your Mac.]] | ||
* [[Eduroam configuration in /Linux/BSD: wpa supplicant]] | * [[Eduroam configuration in /Linux/BSD: wpa supplicant]] | ||
Revision as of 14:25, 14 December 2017
Connecting to an eduroam site should be little or no different from connecting to your home institutions network. You use the same authentication method, encryption and user name/password (or certificate). The only thing that might differ is how you connect to the network. You either use an ethernet connection or wireless. Using the wireless you might be used to connecting to a certain SSID or it might be that your institution uses the SSID 'eduroam' for it's own users also, in which case you don't have to change your connection profile at all.
Wireless connectivity
For wireless eduroam areas / buildings are SSID 'eduroam' (small letters). SSID should normally be sent out, but some places may not. You will also perhaps be able to see the eduroam logo (at the top in the left corner of this page) on posters or signs.
Configuration overview
- Authentication: WPA/WPA2
- EAP type: PEAP
- Tunneled Authentication Protocol (PEAP): MS-CHAPv2
- Full identity / username and password
- WLAN SSID: eduroam
- Encryption (WLAN): TKIP (WPA) or AES (WPA2)
- IP address: DHCP
Example configurations
We've created step-by-step instructions for how to configure some of the most common clients.
NB! Mac users experiencing problems with eduroam may have expired certificates on their computer. To solve this, try to enter the keychain and select certificates at the bottom left. These certificates will have names like nps or radius.uib.no. Here's more information about how to delete keys from the Keychain on your Mac.
Technical description
Access to an eduroam network can be offered through an ethernet connection or wireless. All sites in Norway use IEEE 802.1X authentication and wireless networks are TKIP encrypted. Some locations also offer an option for AES encryption. IEEE 802.1X authentication with TKIP encryption conforms to Wi-Fi Protected Access (WPA) while IEEE 802.1X authentication with AES encryption conforms to the IEEE 802.11i standard (and WPA2).
IEEE 802.1X is able to use various authentication protocols through the Extensible Authentication Protocol (EAP). The protocols in use in our networks provide mutual authentication, checking the identity of both the authentication server and user. These protocols are TLS, TTLS or PEAP.
All of these methods require the public certificate of the Certificate Authority (CA) that has issued the certificate of the authentication server. The client will use the CA public certificate to check if the authentication server's certificate is valid.
TLS requires the user to have a personal digital certificate issued. The authentication server will check if the user's certificate is valid.
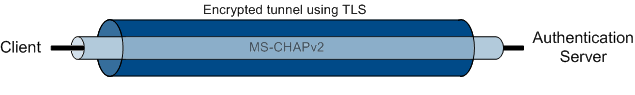
TTLS and PEAP are similar methods that both utilize the authentication server's certificates to create an encrypted tunnel using TLS. This makes it possible for the user to safely transmit a username and password. The username and password is transmitted using MS-CHAPv2.
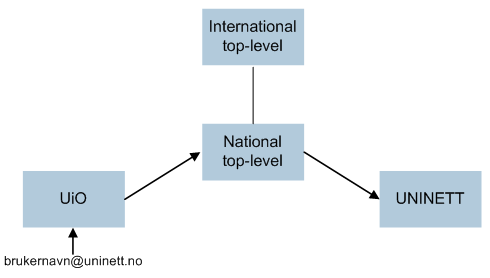
At your home institution your local RADIUS server checks if you have the correct authentication. When you connect to another eduroam site, that RADIUS server will forward your authentication request to the next level RADIUS server in a hierarchy of servers. Every national top-level RADIUS knows where to forward authentication requests from users within its nation. Requests from users from other countries are forwarded to an international top-level RADIUS server which in turn forwards it to the correct country. To have all this forwarding work each user must be uniquely identified. The user name must be followed by '@', organization and country. I.e. if your user name is "brukernavn" and you work at UNINETT in Norway, your full identity/user name should be "brukernavn@uninett.no". If you neglect to use your full identity/username you might still be able to log on at your home institution but other institutions will not be able to check your identity and you will be denied access.
You must have installed a client on your computer that is able to authenticate using IEEE 802.1X, the correct EAP protocol and employ the required encryption method. There are many such clients available with support for Linux, Windows and OS X. For Linux there is the Xsupplicant or if it is for a wireless network: wpa_supplicant. Windows XP SP2 has built-in support and so has OS X. There are also numerous third-party clients.
Once connected and properly authenticated and IP address is dynamically provided by a DHCP server.